Posted on May 17, 2023
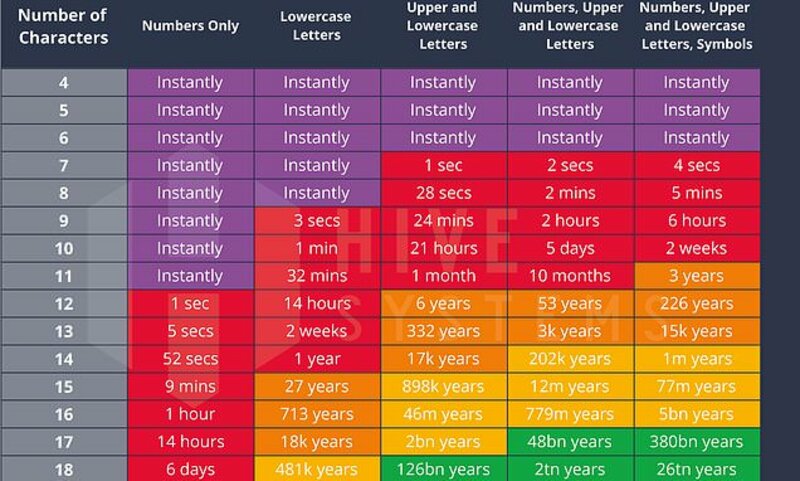
How weak is YOUR password? Graph shows how fast hackers could break it
4.98K
14
7
5
5
0
Posted >1 y ago
Responses: 6
As one of the cybersecurity guys around here, allow me to add context. To crack a password, one must first get the hash file containing your password. In Windows, this is typically known as the SAM file, but there are others too. The point is, generally if the threat actor (TA) has these hashes, it's a pretty good bet they already own your network. However, good passwords can help with preventing escalation or propagation. In the end, your job is to 1. Make it not guessable (which is the reason for the complexity requirements) so that it cannot be brute forced and 2. Make it hard to crack by using the recommended 15 (yes, 15-character password length).
I mentioned brute force, so to explain the difference of that technique vs password cracking: Brute force is attempting to guess the password through straight up logon attempts (in which the TA might have a list of known usernames, or may be brute forcing those too). Back in the day within the DoD, we commonly were able to log on to the local server accounts using the user "admin" and password "password". But if I know your rules for logon (say 3 attempts in 45 min, lock the account), I can customize the brute force to attempt 2 guesses and then wait 45 min before attempting that same user again (while attempting the next ones on the list). This technique, however, can and should be caught through a brute force detection control (if employed).
In the end, I recommend the following for passwords:
15 characters minimum with alphanumeric (upper/lower case) and special symbol characters. And to make it easy to remember but hard to crack (even with just alpha upper/lower characters) think of a phrase/quote from a speech, movie, or book, and you can either type part of it out as a whole, or take the first character of each word. For example (and no, these are not, nor ever have been my passwords):
From the movie Top Gun:
I feel the need, the need for speed - Ifeeltheneed,theneedforspeed (28 chars) These tend to be the easiest to type out once you train your mind to not use spaces (some passwords won't allow spaces).
Or the following quote:
You can lead a horse to water, but you can't make it drink - Ycl@h2h2o,bycmid (16 upper/lower alphanumeric, spec sym chars)
Also, PLEASE do not use the same passwords for various work logons (like the same pw for NIPR/SIPR/JWICS), and do not use your work passwords for personal accounts (home PC, banks, shopping, etc). I recently took part in the incident response for a breach of a company which was hit with ransomware. At least one of the VPs of the company likely had their bank accounts emptied out because that person used the same password for both work and the person's bank.
I mentioned brute force, so to explain the difference of that technique vs password cracking: Brute force is attempting to guess the password through straight up logon attempts (in which the TA might have a list of known usernames, or may be brute forcing those too). Back in the day within the DoD, we commonly were able to log on to the local server accounts using the user "admin" and password "password". But if I know your rules for logon (say 3 attempts in 45 min, lock the account), I can customize the brute force to attempt 2 guesses and then wait 45 min before attempting that same user again (while attempting the next ones on the list). This technique, however, can and should be caught through a brute force detection control (if employed).
In the end, I recommend the following for passwords:
15 characters minimum with alphanumeric (upper/lower case) and special symbol characters. And to make it easy to remember but hard to crack (even with just alpha upper/lower characters) think of a phrase/quote from a speech, movie, or book, and you can either type part of it out as a whole, or take the first character of each word. For example (and no, these are not, nor ever have been my passwords):
From the movie Top Gun:
I feel the need, the need for speed - Ifeeltheneed,theneedforspeed (28 chars) These tend to be the easiest to type out once you train your mind to not use spaces (some passwords won't allow spaces).
Or the following quote:
You can lead a horse to water, but you can't make it drink - Ycl@h2h2o,bycmid (16 upper/lower alphanumeric, spec sym chars)
Also, PLEASE do not use the same passwords for various work logons (like the same pw for NIPR/SIPR/JWICS), and do not use your work passwords for personal accounts (home PC, banks, shopping, etc). I recently took part in the incident response for a breach of a company which was hit with ransomware. At least one of the VPs of the company likely had their bank accounts emptied out because that person used the same password for both work and the person's bank.
(4)
(0)
It’s getting harder and harder to find one I haven’t used. Good thing numbers go to infinity, CSM Chuck Stafford
(2)
(0)
CSM Chuck Stafford
What!?! Ain't nobody got time for that! Seriously though, it's great that you have a strong string for security -- 'Opportunity makes a thief' as Tom Paine says and you are not an opportunity
(1)
(0)
Read This Next


 Uncategorized
Uncategorized Cybersecurity
Cybersecurity Hacking
Hacking Computer & Network Security
Computer & Network Security Computers
Computers


